March 🌷
Hashing for input, and more...
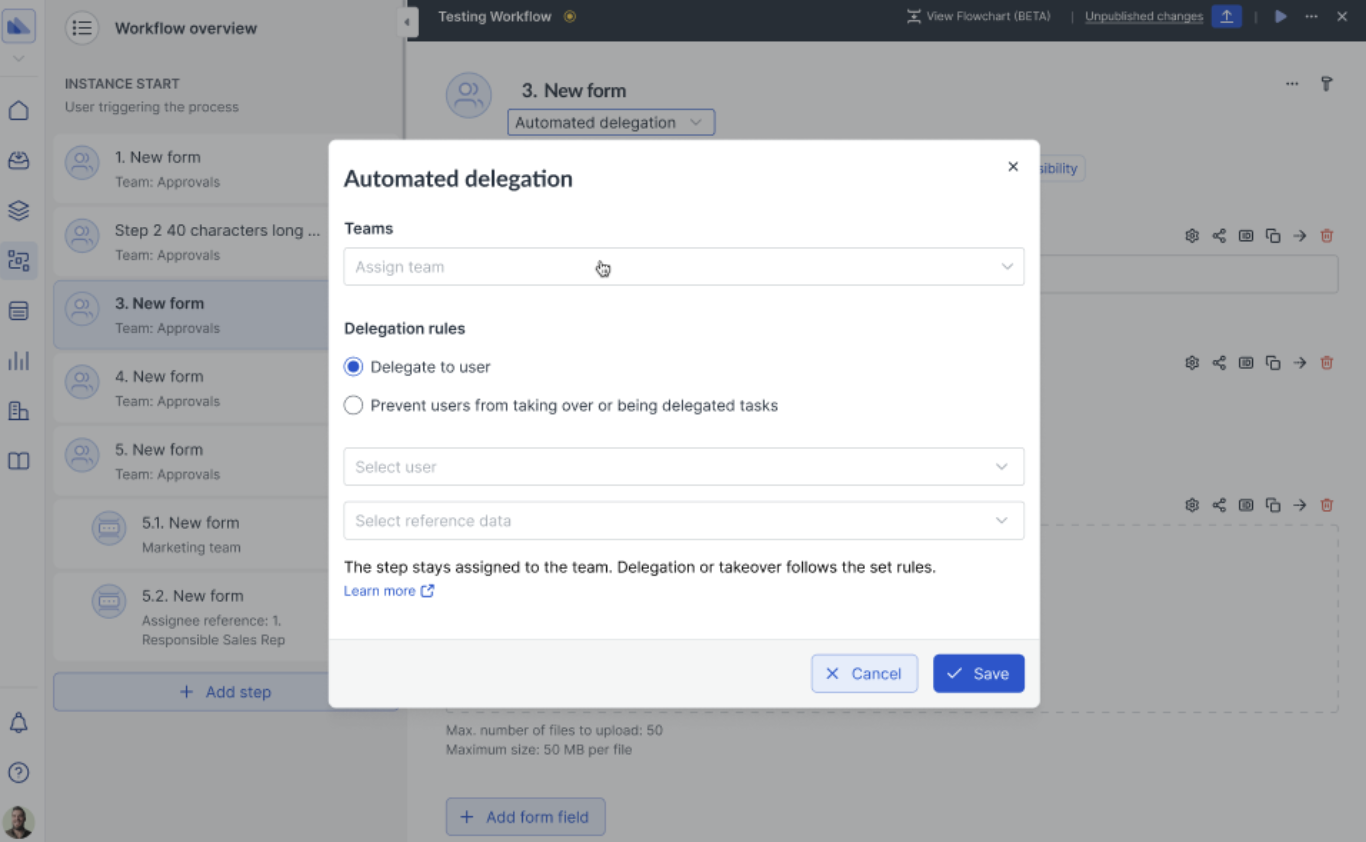
Smarter task assignments with automated delegation
When a step is assigned to a team, it lands in the Next Matter team inbox, where any team member can pick it up. But what if certain tasks should always go to the same person—or never to the same person?
With automated delegation, you can:
- Ensure continuity by assigning related tasks to the same user.
- Enforce security or approval policies by preventing the same user from completing certain steps.
Set it up once, and let your workflows run smoothly! 🎯
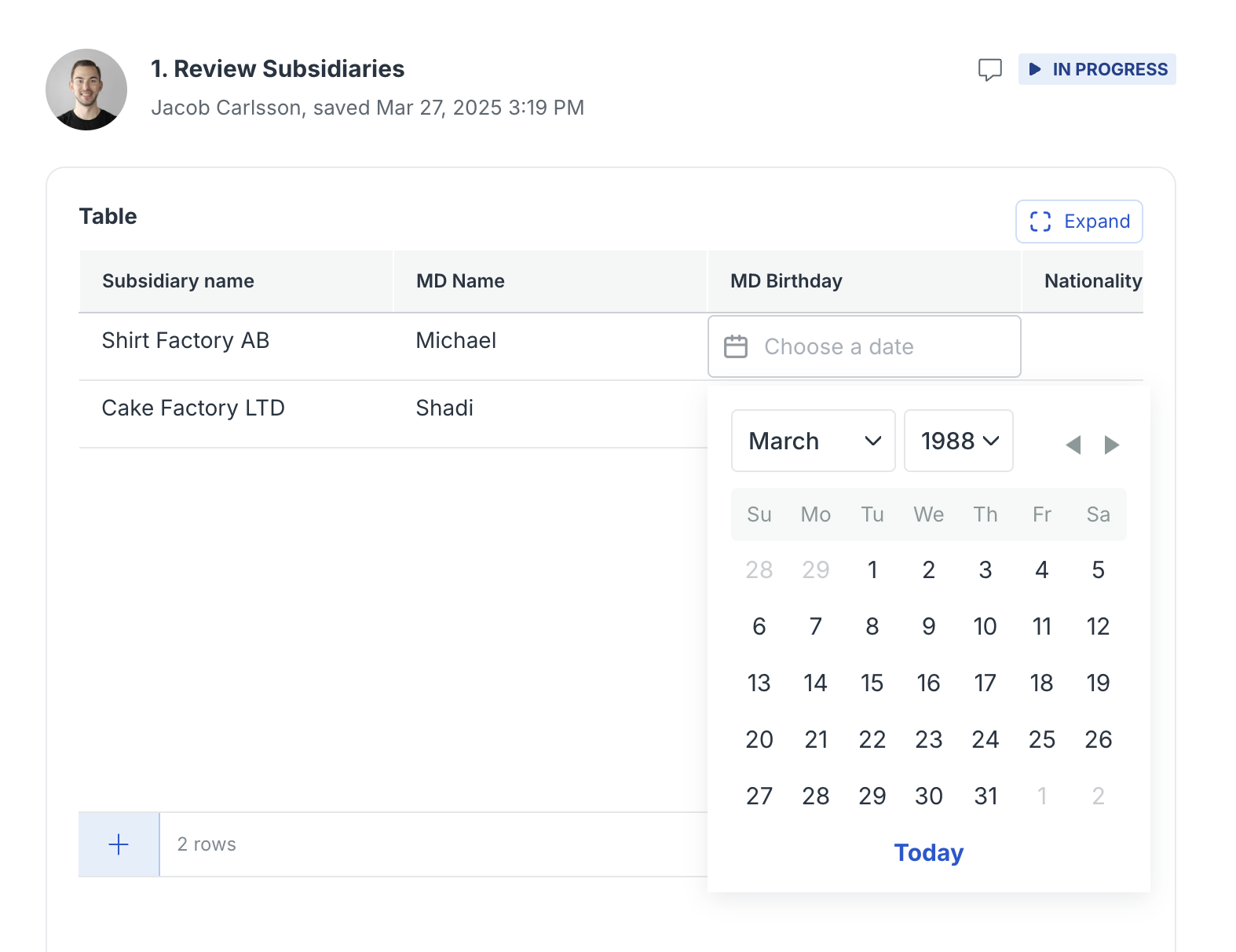
Date field for tables
We’ve just introduced a new input type to the table form field - date fields!
Builders can now easily collect date inputs from users through a user-friendly date picker directly within the table. This is perfect for workflows that require tracking of due dates, scheduling, timelines, or any other time-based data.
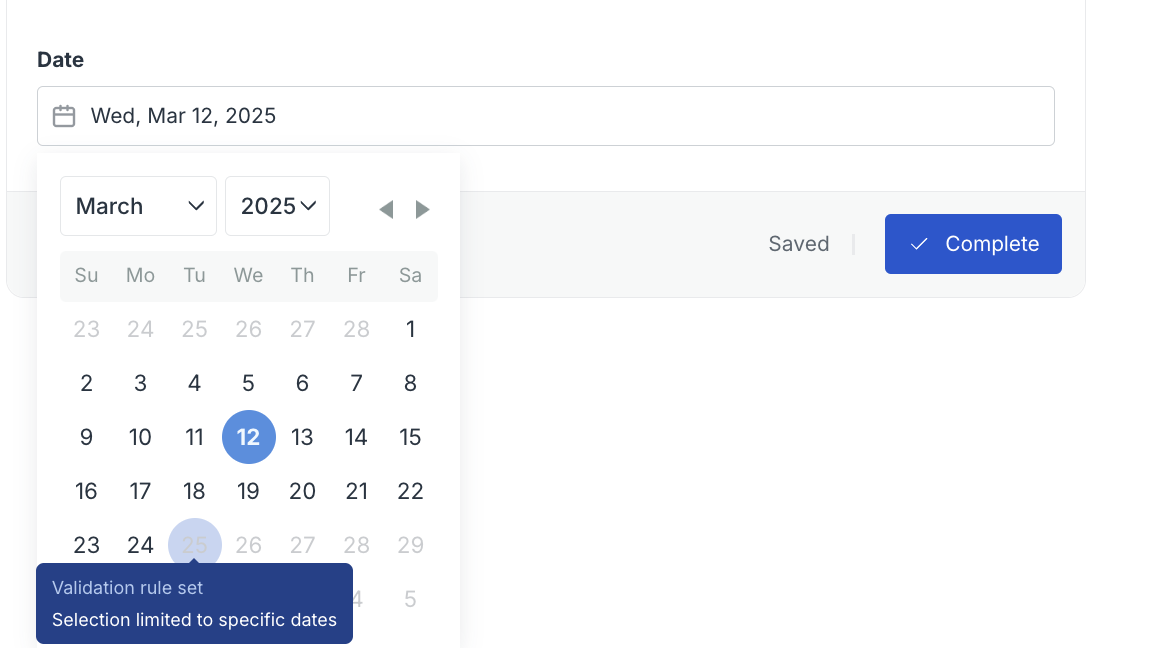
Validation rules for Date input
Builders can now define validation rules for Date fields to restrict input to specific ranges. These rules help ensure that entered dates meet important criteria based on the step or instance context.
Examples of supported rules:
- Date must be after the instance start
- Date must be before the deadline of a specific step
- Date must be at least 18 years ago
- Date must be no more than 5 days after the step activation time
For details, see Field validation
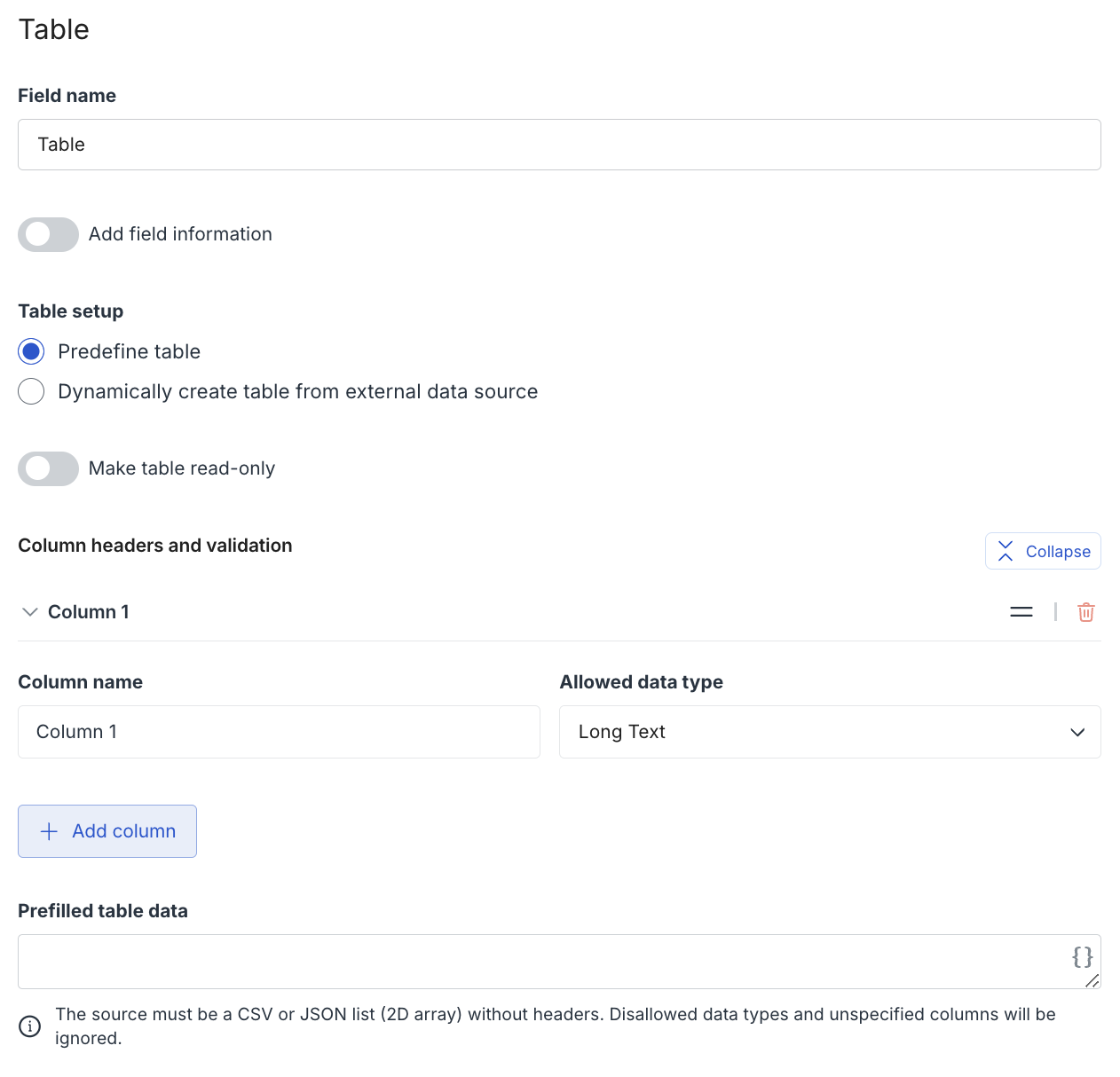
New in table form Fields: Long text inputs!
We’ve just added a brand new input type to the table form field: long text fields!
This update allows teams to collect more detailed responses from end-users — perfect for structured notes, rich descriptions, or multi-line inputs.
✨ Key Benefits:
- More space for writing: Supports line breaks (Shift + Enter) for better formatting
- Improved readability: Wider and taller input fields
- Auto-wrapping: Reviewers can read full content at a glance without scrolling
- Newlines (\n) from external data sources are respected (following JSON standards)!
Quick action hashing feature
This new quick action allows you to concatenate multiple strings and generate a secure hash of the combined result. Hashing is essential for password storage, data integrity, and digital signatures, ensuring security while optimizing storage and retrieval speeds. It can be used to:
- Securely store user credentials
- Verify file authenticity and prevent corruption
- Ensure document authenticity
- Speed up database queries with unique identifiers.
For details, see Generate hash.
